What Organizations Should Watch For
One troubling development is the rise of double-extortion schemes. Rather than only encrypting files, attackers steal copies of a company’s data and threaten to leak it publicly if the ransom is withheld.



Early spear phishing attacks were relatively simple, relying on publicly accessible data like corporate email formats and job titles. Attackers would pose as a high-level executive, emailing finance teams with “urgent” requests for payments.
Even before remote collaboration tools took center stage, insider threats were a longstanding concern. Notable data breaches in the early 2010s showed the extent of damage a single person with privileged access could inflict.
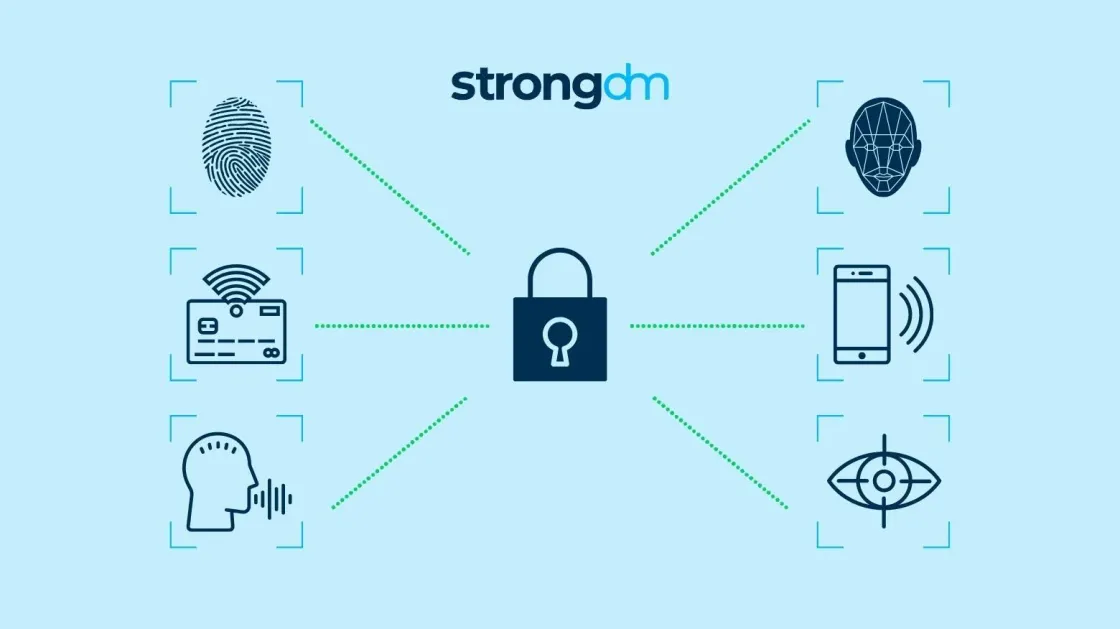
Authentication challenges have plagued organizations for decades. Traditional passwords not only burden users—leading to insecure practices like writing them on sticky notes or recycling them across multiple platforms—but also invite attackers to utilize brute force techniques.

Early spear phishing attacks were relatively simple, relying on publicly accessible data like corporate email formats and job titles. Attackers would pose as a high-level executive, emailing finance teams with “urgent” requests for payments.

Authentication challenges have plagued organizations for decades. Traditional passwords not only burden users—leading to insecure practices like writing them on sticky notes or recycling them across multiple platforms—but also invite attackers to utilize brute force techniques.
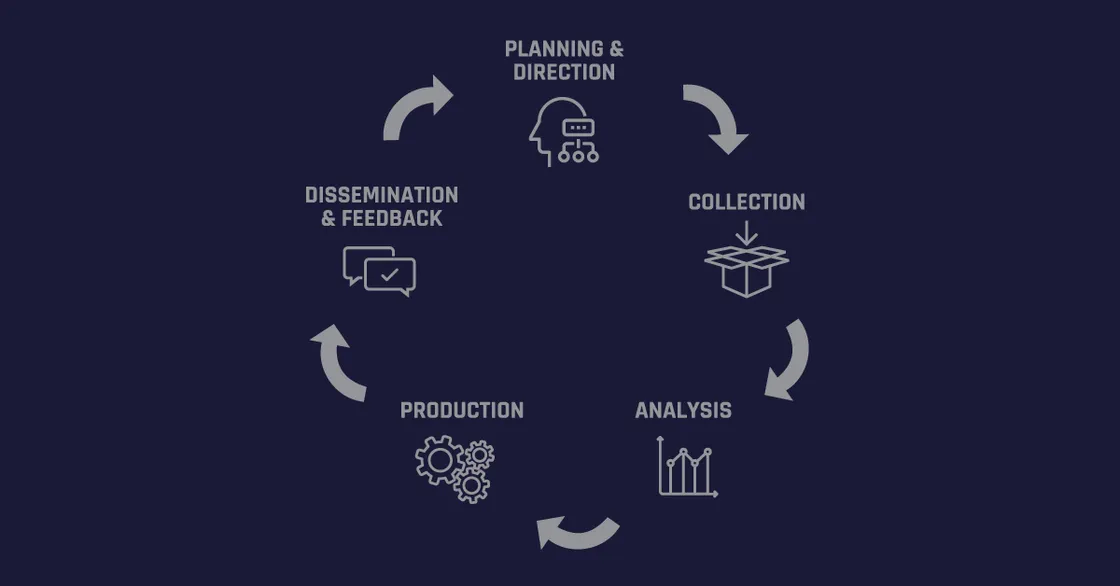
Modern threat intelligence goes beyond collecting headlines about the latest malware outbreak. Skilled analysts rely on advanced tools, open-source data, and specialized vendor feeds, linking seemingly unrelated events to create a bigger picture of how an adversary might operate.


Modern threat intelligence goes beyond collecting headlines about the latest malware outbreak. Skilled analysts rely on advanced tools, open-source data, and specialized vendor feeds, linking seemingly unrelated events to create a bigger picture of how an adversary might operate.




Conventional hacking required a tedious process of testing exploits on various systems to see which ones might yield a result. Now, machine learning tools can ingest enormous libraries of known flaws, then systematically attempt permutations across a range of targets at scale.


One reason for XDR’s sudden appeal is the ongoing shift toward decentralized computing. As organizations adopt hybrid and multi-cloud environments, employees and contractors increasingly connect from diverse networks and devices.